K8s - User and Groups
In this post, we will see how user and group works. Technically, there is no concept of user and group management in K8s.
But, K8s has something called "Service Account".
When K8s is installed from scratch, every namespace has "default" service account and it has admin access to perform actions.
It is not practically possible to use "default" service account for every actions. From security point of view, we need to give fine grained and required access.
K8s has 2 important things in the space of "Access Management".
Role and RoleBinding [Namespace Scoped]
Role: Create a role with actions allowed actions on the resources.
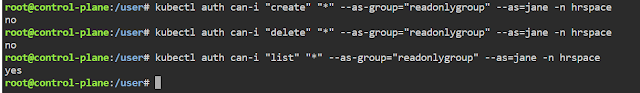
Let's say I want to create a readonly role. Using the role users can only view the resource and cannot perform actions like create, modify, delete.
Rolebinding: Attaching the role to a user, group and service account is called "Role Binding".
Now, we can see the role "pod-reader" is attached to the users "jane", "smith", "paul" and group "readonly-group".





Comments
Post a Comment